With the ever-growing compliance requirements in businesses, it’s important to have policies in place that can help manage and monitor compliance. In this blog, we’ll be discussing the best practice to follow for compliance policies in Intune for Windows.
By following these best practices, you can ensure that your company is compliant with all the relevant regulations and standards.
Make sure you have Intune license before proceeding with the compliance policy
What are compliance policies in Intune?
Let’s understand compliance policy first. Compliance policies are guidelines that help protect your company’s data and ensure regulatory compliance. Intune is a great way to automate your compliance policies, saving you time and hassle using dynamic groups if you put those in use.
With Intune, you can easily create and enforce policies that govern access to data, user behavior, data security, data residency, data retention, data access, and data transport.
You can also use Intune to monitor compliance status and access reports that show the status of policy compliance.
When do you need to create compliance policies?
When it comes to compliance policy, The answer to this question largely depends on your company’s compliance needs. You must look at the requirements that Intune offers for the windows platform and then select those requirements. We will discuss all windows related requirements in this post.
You may need to create policies when you first implement Intune, when you upgrade to a more advanced version of Intune, or when you make changes to your compliance settings.
If you’re still unsure, it’s always a good idea to speak with your Intune Administrator. He or she will be able to help you understand your company’s compliance needs and create the appropriate policies.
Let’s get into this!
Windows Best Practice for Compliance Policy
When it comes to compliance, it’s important to know the right policy to put in place. Windows has some great compliance policies that can help you implement from your Intune portal.
Make sure to get familiar with them and use them to create the best possible compliance environment for your business. Personally, my thought is every setting available in the compliance setting is important and at least you should look at them once. For Instance;
Custom Compliance Policy
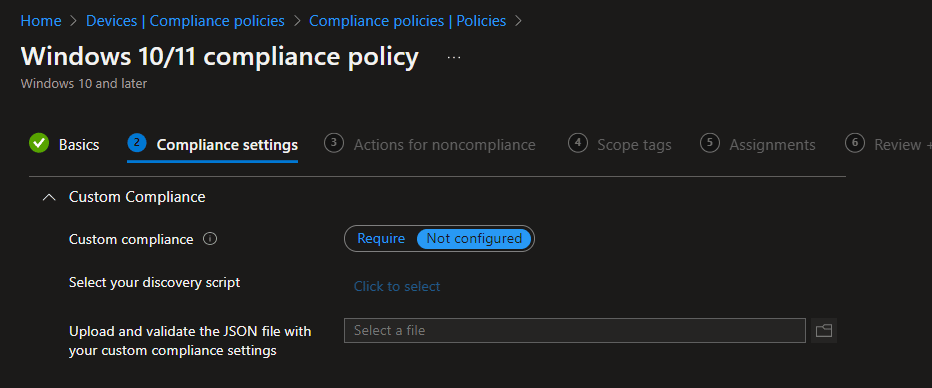
This is a new feature that allows admins to create a custom compliance policy for windows and Linux devices. You need to create a JSON file for which you can the details here.
To learn more about custom policy I would suggest visiting this Microsoft doc.
Device Health
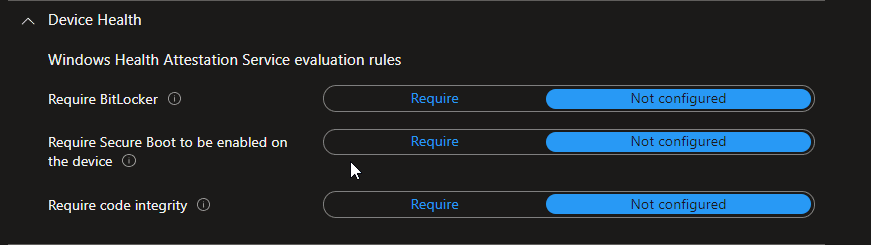
Device health is extremely important to ensure device compliance with company policies.
If you are deploying the BitLocker policy to your windows devices, then you should deploy the “Require Bitlocker” device compliance policy. This will allow you to make devices complaint that only has BitLocker enabled.
Plus, If you are using a conditional access policy along with a compliance policy then devices that are not compliant will not be able to access cloud resources.
Similar to Bitlocker, Device health also has settings for “Requiring Secure Boot to be enabled on the device” and Requires code integrity.
Require Secure Boot to be enabled on the device
This setting will validate that secure boot is enabled on the device. Secure Boot is a security standard developed by members of the PC industry to help ensure that a device boots using only software that’s trusted by the original equipment manufacturer (OEM).
Require code integrity
Code integrity is a threat protection feature that checks the drivers and system files on your device for signs of corruption or malicious software. You can also attest code integrity using compliance policy.
Important note: Code Integrity needs a secure boot to be turned on the device.
Device Properties
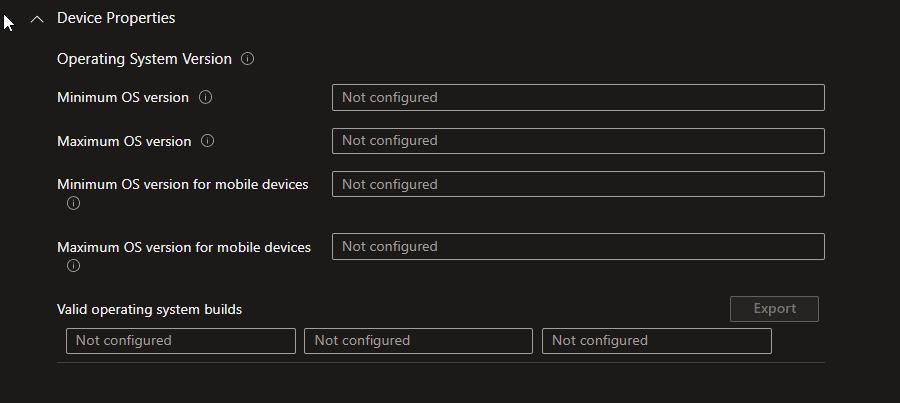
Under this section, you will find various settings specifically targeting devices’ OS versions
This will allow you to make sure that your devices are running on the minimum OS version you selected. If they are not, then they will show no compliance, and as explained above, if you use conditional access with a compliance policy then devices that are not compliant won’t be able to access your cloud resources.
Configuration Manager Compliance
This setting is only applicable to co-managed devices. More on this is available on this article
System Security
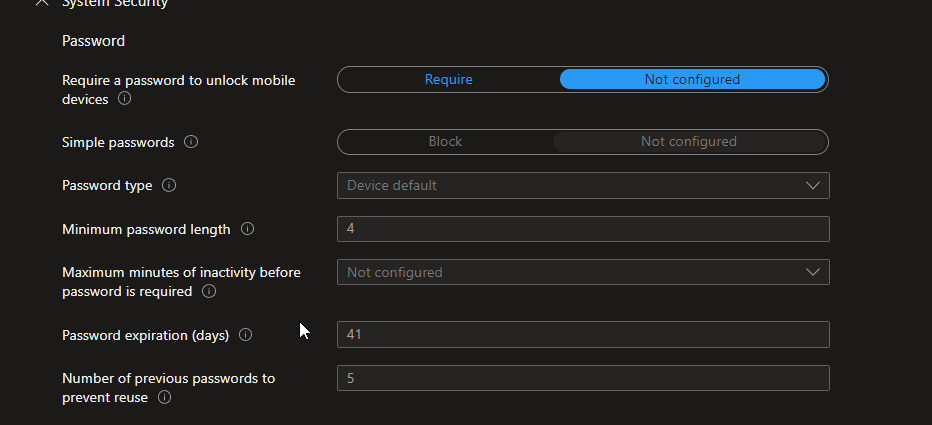
System security is mainly focused on the password and its requirements. Now note here. these requirements are not for your Azure AD user logon. These are for the local user accounts that you may have or create on the devices.
According to me, these settings are not really needed until or unless you are using LAPS or paying special attention to local user credentials.
Your azure ad user logon will not be validated by these policies.
Encryption
Require encryption of data storage on the device also verify the BitLocker encryption on the device bit with a different mechanism than “Require BitLocker”
But at the end of the day, you are validating the BitLocker encryption.
Device Security
Devices security is mainly focused on ensuring some device security features like the Presence of a Firewall, TPM, Antivirus, and Antispyware.
If you mark these Require, Compliance policy will validate, and mark compliance or not compliant on the basis of the setting’s presence on the device.
Defender
You need defender integration enabled with intune to utilize this setting to its full potential. This setting will check for Microsoft Defender Antimalware, its minimum version, Security intelligence, and real-time protection which you do need to turn on via Intune, or from the defender.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is a compliance policy feature that helps you to make the device compliant on the basis of risk score factors that you will determine from the defender portal.
Once you finalized your option selection, now is time to have some more fun with the compliance policy, Click Next, and you will see a page called the action for non Compliance.
Actions for noncompliance
This is a very cool feature. Action for Non-Compliance will allow admins to make some automation the moment device became not compliant.
For example, I can send an email with a designated template to the user to notify them that their device is not compliant and has to meet the requirement in order to access the cloud resources. Below is an explanation of the actions you can do with these options.
Mark device noncompliant
If you are not compliant with Intune policies, your devices will be marked as non-compliant. If you use conditional access along with compliance this can have a number of consequences – from reduced functionality to permanent loss of data. Make sure you are up to date with all Intune policies and take appropriate action when necessary. Prevention is always better than cure!
Send an email to the end-user
Emailing users who are not following your policies can help ensure compliance and improve user experience. Keep the email short, to the point, and easy to read – it’s important that people understand what they need to do without having to read a long paragraph.
Retire the non-compliant device
You can also add their device to the retire list with the option of days to defer. Which will remove the non-compliant device from intune after a specific number of days.
Here is a detailed explanation of windows compliance policy best practices you can utilize in your network via Intune. If you would `like to see other blogs post about best practices for other platforms like macOS, ios, and android, do rate this blog post and subscribe to the newsletter.